

I once wired my whole ass house for ethernet. (Before realizing I was colorblind nonetheless.) Instead of studying.
Never underestimate how you can use study procrastination as a push force for other shit. (Unless you’re a dipshit like me and do it with an imminent exam)


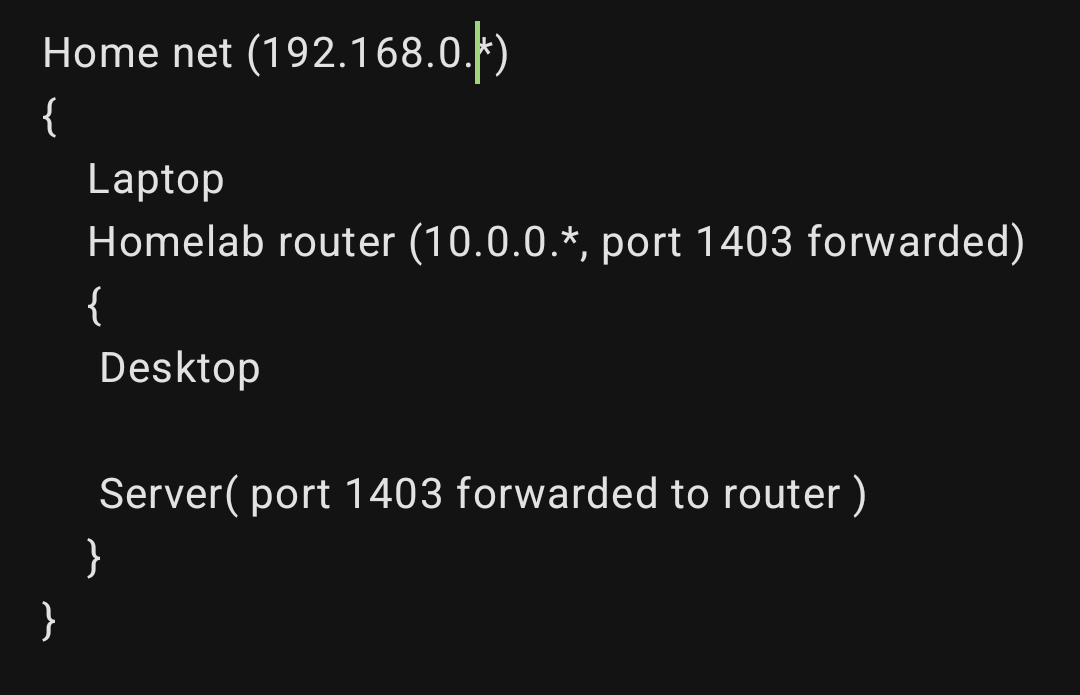




Liking computers in general and switching to Linux at 15 out of desperation.
After that all it took was getting an shitbox pc as a hand me down to make me go “Linux is also used on servers right? Shouldn’t be too difficult to setup something.” And that’s how I got the bug.